SmartyGrants Single Sign On (SSO)
Overview
SmartyGrants is a web-based software-as-a-service (SaaS) product that allows organisations to run grant programs and receive online applications. SmartyGrants offers SAML 2.0 browser-based Single Sign-On to provide the following benefits:
Customers can centrally manage users' access to multiple applications, via their SAML Identity Provider (eg. Entra ID, Okta, etc).
Users have fewer passwords to manage.
Organisation password policies are automatically enforced.
Multi-factor authentication can be used - where supported by the customer's SAML Identity Provider.
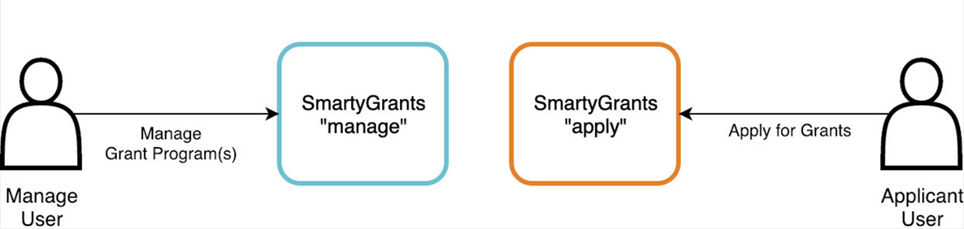
SmartyGrants has two key components - a Manage Site where funding organisations can manage their grant programs, and an Applicant Site where applicants can register themselves and apply for grants published by a funding organisation. SmartyGrants currently offers Single Sign-On (SSO) for manage users only. Applicant users must register using their email address and nominate their own password.
Some key points to note about SmartyGrants' SSO feature are:
Customers must operate their own SAML Identity Provider (IdP) that will handle their users' logons, such as Entra ID.
Once a SmartyGrants Account is configured for SSO, it will either apply to:
All users of the Account (default) or;
All users of the Account with particular email domains as specified by you (e.g. only users with an @example.com email, excluding external users such as assessors). See External users and SSO.
Regardless of your specific configuration above, all affected users will need to be provisioned in your Identity Provider by the time SSO is applied to your live Account.
SmartyGrants at no point has visibility of the user’s password for SSO logins.
SmartyGrants does not directly support multi-factor authentication (MFA). However, many SAML Identity Providers provide this feature.
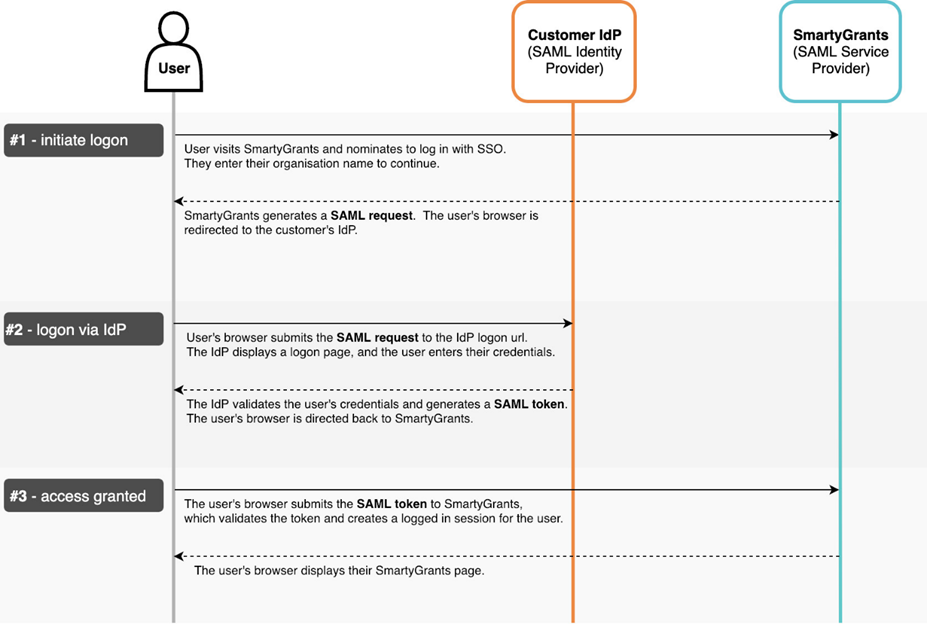
The sequence diagram below illustrates the exchange of data between the end user's browser, SmartyGrants and the customer's IdP:
User login experience
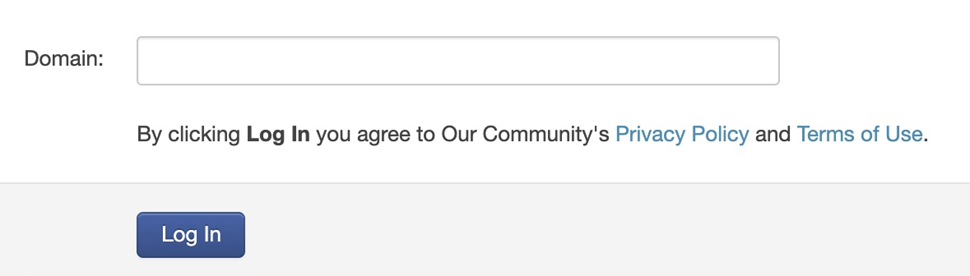
Manage users may access a dedicated SSO login URL within SmartyGrants to log in using SSO. This URL is https://manage.smartygrants.com.au/login/sso. The user will be asked to enter their domain - which is defined as part of the technical configuration (see section below).
After entering a valid domain, the user will be taken to the login screen of the customer's SAML Identity Provider, and will be returned to SmartyGrants once they successfully log in.
It is also possible for end-users to add the domain directly to the SSO Login URL, so that it can be bookmarked, linked to from an internal portal/intranet, or accessed by an auto sign-in agent - e.g.: https://manage.smartygrants.com.au/login/sso/<<customer-domain>>. This streamlines the login process by allowing users to bypass the step of entering their domain every time they log in.
User provisioning and authorisation
SmartyGrants manage users have roles with varying access levels, including an administrator role that can manage the access levels of all other users in the Account, including adding and removing users. SmartyGrants does not currently support automated user provisioning for SSO - each user must be added by an administrator via Settings > User Access > Add User in the Manage Site. This process defines the user, using their email address as their username, as well as the permissions the user will have within the Account. Only once this is defined, and the user has also been provisioned in the customer's Identity Provider (IdP), can the user successfully access the Account.
SAML responses returned by the customer's SAML IdP must contain the user’s email address. Multiple SmartyGrants features require users to have a valid email address, and the email address is used as the username by the system.
External users and SSO
By default, SSO applies to every user in a SmartyGrants Account which may include external users such as assessors. However, it is possible for SmartyGrants to restrict your SSO setup to users with certain email domains, allowing other external users to log in via the native login method (i.e. SmartyGrants username and password), bypassing SSO. This is relevant for organisations that cannot provision external users to their organisation's SAML IdP (for example, assessors external to the organisation).
On request, SmartyGrants will apply a setting to the SSO configuration to restrict it to users with certain email domain/s that you specify. This action must be done by the team at SmartyGrants.
For example: a SmartyGrants Account has SSO enabled. By request, this Account has been configured to require any user with the domain 'example.com' in their username (i.e. olly@example.com) to log in using the SAML IdP. Any user with any other domain in their email address (i.e. assessor@gmail.com or user@consultancy.com) will not be bound by the SSO requirement and will log in to this Account with a native SmartyGrants username and password.
In the example scenario above, only users from the organisation (with @example.com) email addresses are required to be provisioned in the Oranisation’s SAML IdP.
Note: Multiple SSO Email Domains can be configured on a single Account’s configuration.
Single Sign-On technical configuration
SmartyGrants requires the following information to enable SSO for your Account:
Entity Id - A unique identifier from the Identity Provider. This is often a URL.
Domain - A domain name for your organisation that is meaningful to your users. If a Manage user accesses https://manage.smartygrants.com.au/login/sso this is the "Domain" they will be prompted to enter (see "User login experience" above).
SSO Metadata XML or Metadata URL - The metadata provides key information for SmartyGrants to complete the authentication process, including details of the signing certificate that the IdP will use when signing SAML responses/tokens.
Login URL - The login URL for the IdP, which SmartyGrants can redirect users to in order for them to log in.
Username Attribute Name - SmartyGrants uses email addresses as the unique identifier for a user. By default, SmartyGrants will look for a user's email address in the Subject NameId of the SAML response, which should be in "urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress" format. Alternatively, the IdP's SAML response/token may include claims/attributes of a successfully authenticated user, and the user's email address can be sourced from one of these (eg: "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailAddress").
(Optional) SSO Email Domain - An email domain, or multiple domains, can be defined and applied by SmartyGrants to the SSO configuration. Please see External Users and SSO above for more information.
Single Sign-On implementation process
The process to have SSO configured on a SmartyGrants Account is as follows:
An administrator of the Account's Manage Site emails SmartyGrants requesting SSO be enabled on the Account.
SmartyGrants requests the required information as detailed above in Single Sign-On technical configuration. This request includes the username (email address) of at least one user who will be testing the configuration.
SmartyGrants receives the required information and creates and configures a test SSO Account, adding the nominated user/s as administrators and notifying the requesting administrator that logging in to the test Account via SSO is ready for testing.
The user conducts testing in the SSO test Account and may add additional users to the Account for further testing. Any issues raised during this testing will be resolved as required.
When testing is concluded, the user communicates to SmartyGrants a date and time to apply the configuration to their live Account.
At the appointed date and time, the SSO configuration is applied to the Account. From that point onwards, users will be required to log in via SSO.
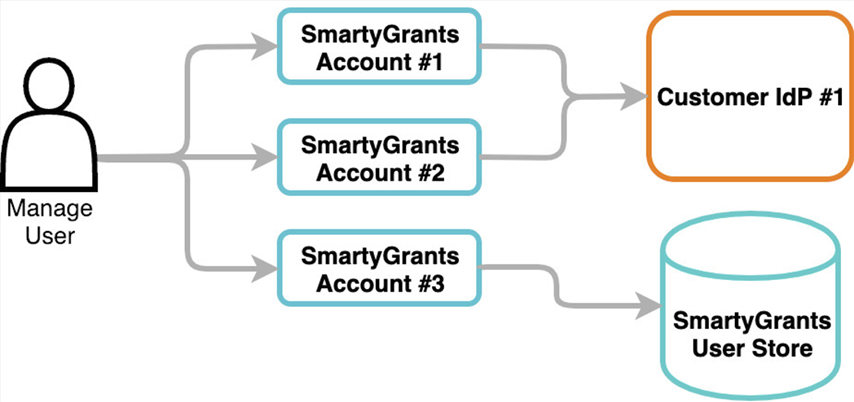
Advanced: Multiple SmartyGrants Accounts
It is possible for a single SmartyGrants manage user to have access to multiple SmartyGrants Accounts. For example, some customers choose to have separate Accounts for different divisions that operate independently. Where a single customer has multiple Accounts configured for SSO, users logged in via SSO will be able to switch between Accounts just as they can for non-SSO Accounts. Where a single user has access to a combination of SSO and non-SSO customer Accounts, an SSO login via the SSO Login Page will provide them with access only to their SSO-enabled Account(s). The customer can also perform a non-SSO login via the regular Login Page to gain access to their non-SSO Account(s).
If you are interested in having SmartyGrants Single Sign On enabled for your SmartyGrants account, please contact the SmartyGrants Service Team.